Vehicle Hacking: A Modern Problem With Minimal Solutions
INTRODUCTION
Have you been paying attention to cybersecurity news and the threats facing the automotive and supply chain industries
This year we’ve seen car thefts through CAN injection attacks, nation-state level attacks on supply chains, and vulnerabilities that affect millions of vehicles. In fall of 2022, Sam Curry discovered API security vulnerabilities in Kia, Hyundai, Mercedes-Benz, BMW, Ford, and in total almost 20 car manufacturers. These vulnerabilities affect millions of vehicles on the road today.
Since the start of the war in Ukraine, Russia has been engaged in a cyberwar against the Ukraine and supporting nations. In October, the Russian military intelligence hacking unit targeted transportation and logistics companies in Ukraine and Poland with ransomware. These state-actors are now attacking NGOs and aid organizations working to supply the Ukraine with food, clothing, and medical supplies.
As a nation and as members of a national and global supply chain we can no longer put our heads in the sand and assume that these cyber threats won’t affect us.
WHY SHOULD YOU CARE?
Hacking vehicles has been around for decades in the defense space and academia is beginning to catch up and catch on with releases of research about vehicle hacking in 2013, 2015, and 2023.
With vehicles becoming more and more tech infused, the threats against them have grown with security lagging far behind. In the next 5 years we will see the rise of software-defined vehicles, V2X (vehicle to everything) technology, and autonomous vehicles hitting the road.

We see it as obvious that these vehicles require cybersecurity to protect their expanded networks, but vehicles on the road today are vulnerable. Each vehicle today is comprised of as many as 150 ECUs or computers. Exploiting a single access point can spell disaster for an auto maker and user.
WHY HASN'T IT HAPPENED?
Breaching a vehicle’s network in a malicious attack was previously a very expensive endeavor. These costs have dropped precipitously in previous years and the tools / technology required to conduct these hacks have become commonplace. In fact, you can purchase a CAN injection device online and have it shipped to your home. Just ask the cybersecurity researchers who had their car stolen using one of these this year.
Ransomware attacks against vehicles hasn’t happened yet simply because there are so many ripe IT systems for the taking, but experts warn it could be the next target for ransomware attackers. As IT cybersecurity improves and hardens against these attacks, vehicles and OT systems become a target for criminals who can shut down physical systems and stop vehicles from operating until a ransom is paid.

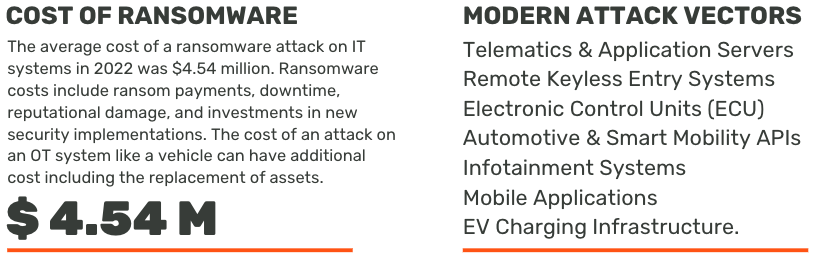
A more severe threat facing vehicles today is the risk of a nation-state level attack. Gaining access to the networks within our countries long haul logistics platforms means a foreign adversary can shut down our US supply lines. Adversaries know if they can halt commerce, shut down supply chains, and prevent goods, resources, and food from being delivered the US would be hindered from assisting our allies in conflicts around the globe.
This might sound like something out of Jack Ryan but the U.S. government is already thinking about this. Organizations like the U.S. Department of Transportation, the Cybersecurity & Infrastructure Security Agency (CISA), and even the White House are taking a more critical look at the cyber threats facing the transportation and automotive sector and offering guidance and regulations to protect vehicles, supply chains, and the automotive sector as a whole.
HOW WOULD AN ATTACKER HACK A VEHICLE?
Physical Attack / Access
In 2022 criminals were able to expose the CAN bus of a vehicle by prying off the headlight of the vehicle. Directly accessing the can bus allowed the criminals to conduct a CAN injection attack with hardware they purchased off the internet. This allowed them to bypass the security measures in place on the vehicle, unlock the doors, start the vehicle and ultimately steal it. In 2016, researchers from the University of Michigan were able to take control of a truck’s throttle and engine brake controls via the J1939 databus of club-cab truck.
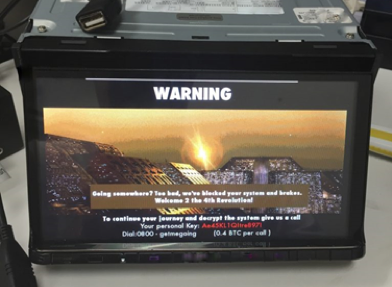
Infotainment Systems
Modern cars make infotainment a selling point. These systems typically contain everything from satellite radio, Bluetooth, GPS, and more systems connected to outside networks. In 2016, researchers at McAfee were able to insert ransomware into a vehicle’s infotainment system over the air. In 2017 researchers were able to hack the infotainment system on a vehicle to pull call histories, contacts, text messages, emails, and even directories from mobile phones that had previously synchronized with the car.
Remote Access
In 2015, Sam Curry and Chris Valasek made headlines by remotely access a Jeep Cherokee and cutting the transmission with a reporter inside. The researchers utilized a zero day exploit (zero day meaning a vulnerability previously unknown by the manufacturer) to remotely access the vehicle. A more recent example includes the ‘bricking’ of John Deere tractors in Ukraine. Unidentified Ukrainians were able to remotely disable $5 million dollars worth of John Deere tractors that had been stolen by Russian soldiers. There were able to do this remotely and effectively turn the machines into bricks.
Cybersecurity Flaws
In 2016, cybersecurity researchers found that telematics units used in over 700 trucks had been left open on the web, accessible to anyone with an internet connection. With the expansion of technology and third party devices being installed in fleets today a single point of failure could be all an attacker needs to enter into a truck or vehicle’s system.
PROTECTING YOUR VEHICLES
Protecting vehicles including passenger vehicles, commercial vehicles, and long-haul logistics is crucial to protecting our nation’s critical infrastructure. Fleet Defender is committed to preventing devastating headlines about cyber attacks against fleets and protecting our national security. We believe that protection today pays dividends tomorrow. Let’s work together to prevent a future headline and keep our cars, trucks, tractors, trains, planes, and ships moving.
LOOKING FOR A MODERN SOLUTION TO VEHICLE HACKING?
Fleet Defender’s AI & ML-powered intrusion detection system was created for the threats of today and tomorrow. Fleet Defender is able to detect attacks not previously seen and alert your team so they can take action proactively instead of just reacting to a threat. Schedule a call with our team today to learn more about Fleet Defender’s software and after-market hardware solutions.
OTHER HEADLINES SURROUNDING PLATFORM CYBERSECURITY AND THREATS
New Bill Targets Chinese Influence on US Ports Amid Cyber Threat Reports – Port Technology
Hackers Steal Car Via The Headlight With CAN Injector Tool – April 2023 – Canis CTO Blog
“There is a vulnerability of millions of cars on the road. If a hacker wants he can just go and do it,” said Roy Fridman, CEO of cybersecurity technology firm C2A Security – Insights from Automotive Cybersecurity 2023 Conference – Forbes
ChatGPT Makes It Easier To Infiltrate Maritime Vessels – Maritime Executive
EV Charging Infrastructure Offers an Electric Cyberattack Opportunity – DarkReading